With the growth of computer literacy, DDoS attacks on websites, hacking of accounts in social networks, monitoring of other people’s e-mails have moved from the category of “force majeure” to everyday life. Some hackers do it out of their “love of art,” while others do it for enrichment.
Therefore, the question is: “how to protect the site from hacking and cyberattacks?” stands in front of all owners of Internet portals and users of online services.
On the Internet, the basic principles of cybersecurity are unified. Your goal is to prevent third-party interference with your own, named network resources. For this:
Create complex passwords. To enter the admin panel, to various mails, accounts, etc. it is necessary to come up with different passwords, and absolutely not related to you. No dates of birth of yourself, your spouse, children, names of your favorite pets, etc. If the attack is targeted, then the attacker collects all such information about the future victim;
Install modern, licensed, special software. This is an antivirus, preferably with a “sandbox” where you can localize and check questionable files, as well as automatic checking of downloaded and existing information;
Do not open, and immediately delete SMS and messages from unknown addresses containing various requests, suggestions;
Do not share passwords and logins with anyone.
This will reduce the risk and increase the security of personal data on the Internet.
Consider the existing attack options:
Cross Site Screening (XSS). Here, all users who visit your page come under attack. A special script or virus is introduced that steals personal data of buyers. With a complete vulnerability to XSS, the administrator options become available.
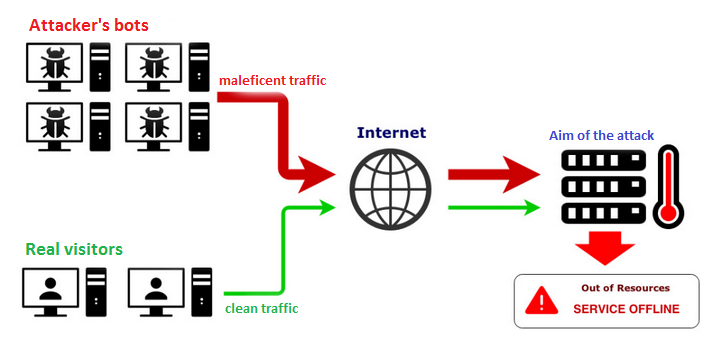
Therefore, protecting sites from attacks includes:
vulnerability analysis to SQL injection and XSS;
installation of security and antivirus programs;
regular testing for the possibility of hacking – pentest;
use of anti-DDoS services;
use and frequent change of complex passwords, if possible, then log in through two-factor authentication;
priority is a secure connection;
regular saving of files and updating of software.
The site can be protected from hacking if you provide multilevel security systems. In fact, the main components play a leading role.
Its reliability is the first line of defense. If it could be constantly hacked, then what kind of security of personal data on the network can we talk about? Read all reviews and gather information about the provider.
When choosing shared or dedicated hosting, give preference to the latter, since then the owner, and not the “local” administrator, bears all responsibility for the operation of the resource. This will give you the ability to set barriers for hackers.
This includes both scripts, CMS and antiviruses, security plugins.
To find vulnerabilities and weaknesses in scripts, special utilities and scanners are used, as well as analysis of the source code.
Modern plugins allow you to protect your site from XSS, spam, and track user actions.
Do not forget that all software works effectively only with regular updates.
Correct configuration of protective systems
closing access to certain directories, etc. for everyone except the owner;
restriction of rights to add / remove / change files or directories;
installation of protection at the entrance to the admin panel, access to it by reliable authentication of the visitor;
a complete ban on the execution of scripts in the download directory, etc.
Google Webmaster will be an excellent instrument for those who start their online business, where you can check the resource for configuration accuracy and security.
The best results come from being a cybersecurity administrator. In addition to the ability to use advanced software, he must fully possess information about the methods of hacking and how to counter it.
The best solution would be to save the content of the Internet resource on the cloud, computer or external resource. In case of hacking, you can quickly restore everything. Sometimes it’s easier to load а clean copy rather than deal with a particularly tenacious virus.
You can also remove any bugs or errors in an isolated environment, make corrections or change the configuration.
SSL certificates provide excellent protection for the connection between the web client and the server. But do not forget that you need to connect from a verified electronic device, ideally using SCP or SFTP protocols.
If you have a completely secure portal, but attackers are seriously interested in you, they will try to find out your personal data in any way and infect at least one of your devices with a virus in order to gain access to the resource.
Phishing is currently showing the highest efficiency. So:
disable geolocation. Today the phone is in your pocket – tomorrow in someone else’s and with full access to everything;
prevent the browser from remembering passwords (auto-complete forms);
install an ad blocker, anti-tracker, anti-mining and other applications that interfere with tracking;
do not follow the links, even if your friend sent them. He could have been hacked too;
When the minimum is known about you, it is extremely difficult to send you a letter or message that you will definitely open. Lack of knowledge about your hobbies, outlook on life will not allow or will make it incredibly difficult to guess passwords.
In cases where you suspect that a “hunt” has been opened on you or your site is not sufficiently protected – contact cybersecurity professionals.
They will find all the vulnerabilities and build a powerful defense.